For AP and client exchanging encrypted data, both need to have the right key(s) installed. Each time a client (Supplicant) associates to an AP (Authenticator), new temporal keys for the pairwise data transmissions are generated, which are unique for each connected client. In case of Broad- and Multicast frames, all clients use the same Groupwise Temporal Key (GTK) that don’t require a new generation for each association.
Transient keys are derived from a master key, a Pairwise Master Key (PMK) could be the passphrase for WPA-PSK or a key derived from the EAP process for WPA-802.1X or WPA-Enterprise. Since transient keys are used, an attacker cannot obtain the master key from sniffing the frames in the air and it is possible to change the PTK without changing the passphrase itself.
The installation of Pairwise and Groupwise Transient Keys (PTK/GTK) is done by the so called 4-Way Handshake with the following flow graph:

Source: Wikipedia
Pairwise Temporal Key Generation
The function to generate a Pairwise Temporal Key (PTK) is known as a Pseudo Random Function (PRF):
PTK = PRF(PMK | ANonce | SNonce | AA | SA)
With ANonce and SNonce as Nonces (Nonce: Number used once) from Authenticator (AP) and Supplicant (client) and the Authenticator’s and Supplicant’s MAC Addresses (AA/SA).
EAP-Key Message 1/4 (ANonce)
As the first message is send from AP to client, this message includes a random number as ANonce for PTK generation at the client. Since the client knows its own SNonce and SA as well as the AA (from Beacons, Probe Response and/or Association Response) and PMK, the ANonce from this message is the only missing information.
EAP-Key Message 2/4
As the Supplicant (client) replies to the first EAP Key message, the client sends the used SNonce as clear text to the AP “protected” by a cryptographic hash (HMAC-SHA1) called Message Integrity Code (MIC) for integrity of of this message the installed key on the client side. The AP will generate its own MIC and compare it the the one in this message, if they match, EAP-Key message 3 is send for key installation. This message also includes the Robust Security Network Information Element (RSN IE).
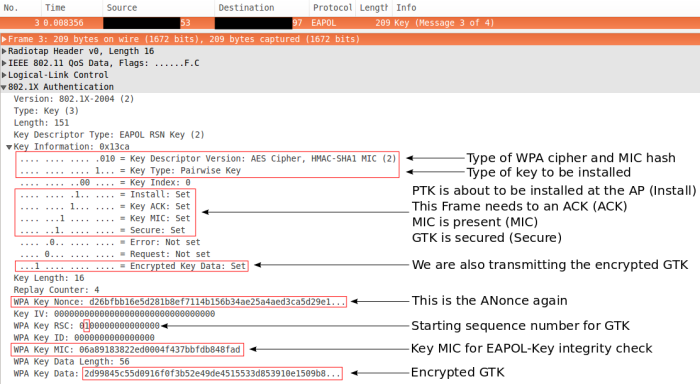
EAP-Key Message 3/4
Message 3 is the last unencrypted key message, as long as no retransmission(s) occur and the pairwise temporal key remains valid. The AP informs the client about the installation of the PTK and the receive sequence counter (RSC) for the GTK. The GTK itself is given in the WPA Key Data field, secured/encrypted with the PTK.
EAP-Key Message 4/4
The Supplicant acknowledges the installation of PTK and GTK afterwards, encrypted Unicast and Broad-/Multicast transmission can start now.
Conclusion
The generation of P/GTKs is quite easy and three of the four frames for the installation are unencrypted, which means that the only secret in PTK derivation is the Pairwise Master Key (PMK). As I will show in another post, the generation of a new PTK for each association to an AP can be shortened to enable a much faster association. This is especially important for client roaming and should not bother any single AP installation at home.
Attacks
In October 2017, postdoctoral researcher Mathy Vanhoef (PhD @ KU Leuven, Belgium) published his research paper on how the EAPoL key exchange can be attacked to read encrypted data without retrieving the actual PMK. He named the attack “KRACK” and here is the link to his paper.
*2017-04-18 Updated due to feedback from apoorva in the comment section*
*2018-01-18 Updated with a link to Mathy van Hoef’s research paper on Key Reinstallation Attacks*